Learn about both hardware and software.
Build your foundation for a lifetime career or business
Designed to allow you to adapt to rapid change in a fast moving industry
Up to 2 yrs f/t - covers
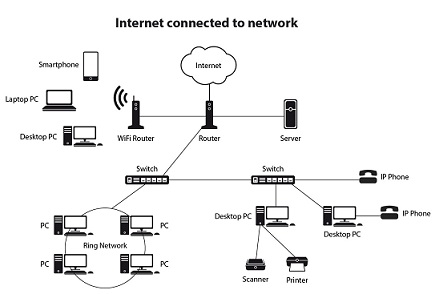
Expand Your Practical Knowledge and Skills in IT
A solid foundation for a career in I.T., this course focuses on developing awareness of industry, knowledge of valuable skills and a capacity to adapt to change in order to remain abreast of what is a rapidly changing discipline. This course does not require any previous IT experience as it takes you right from the basics to a higher level.
The course encompasses a wide range of practical subjects including programming languages such as VB.net, ASP, SQL, Javascript, HTML as well as providing a wide range of elective modules including e-commerce, marketing subjects, editing and more.